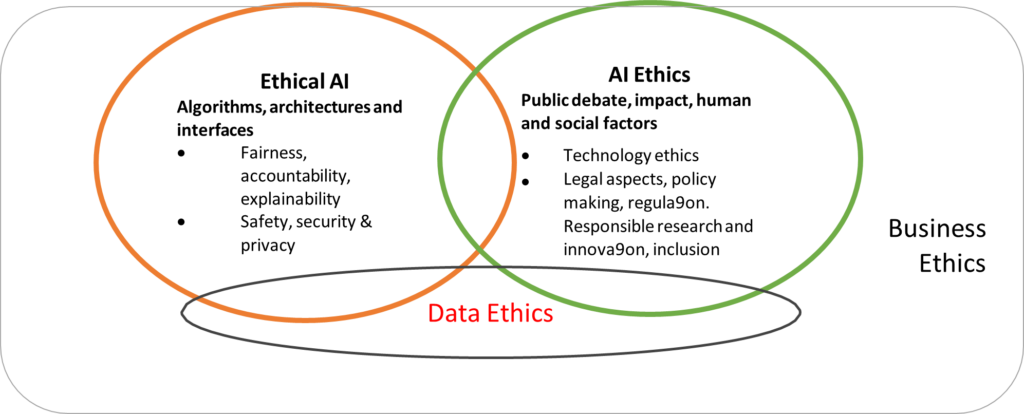
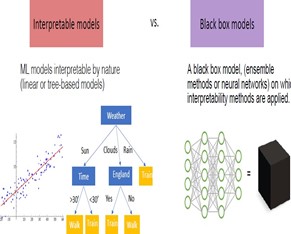
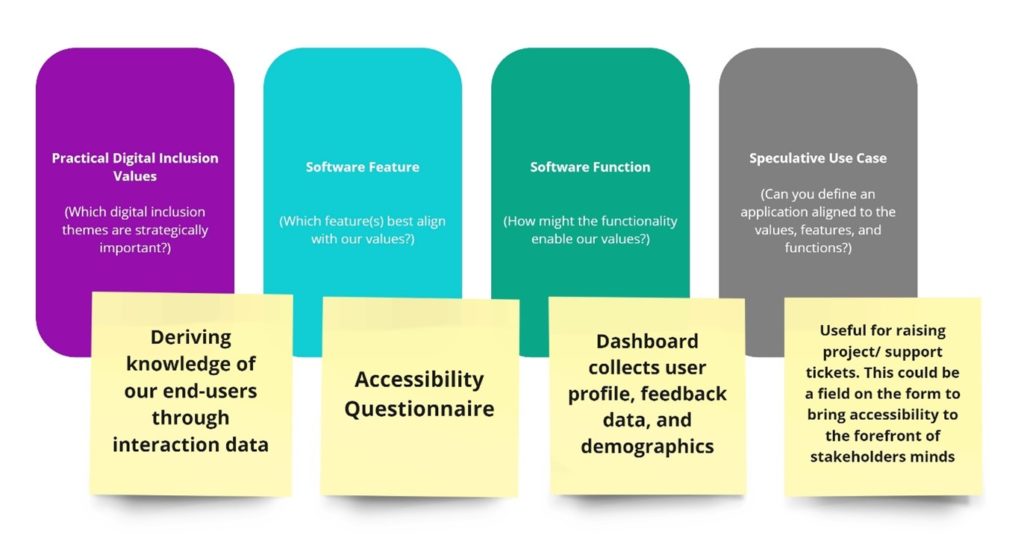
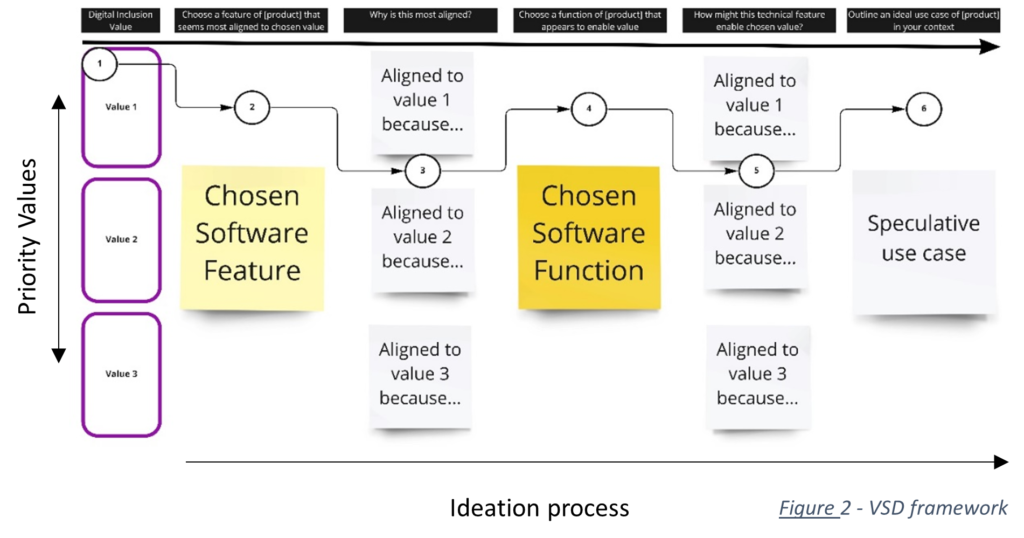
post by Jenn Layton Annable (2020 cohort)
Working as an autistic autism researcher can sometimes be a lonely and distressing experience. Daily contact with academic literature that consolidates pathologising or stigmatising beliefs and constructs can be traumatising. Luckily there is a growing community of autistic autism researchers who, although widely dispersed geographically, come together through digital technology and virtual spaces to offer peer support and collaborate in academic writing and work that counter such narratives with alternatives, grounded in our self-knowledge and awareness. This digital network of neurodivergent researchers, activists and thinkers has also crystalised into the academic disciplines of neurodiversity studies and critical autism studies, containing both scholarship and activism in equal measures.
My first published peer-reviewed paper emerged from this need to counter potentially harmful, clinically situated perspectives. An autistic autism researcher acquaintance Nick Chown raised the matter of the paper Neurodevelopmental disorders and neurodiversity: definition of terms from Scotland’s National Autism Implementation Team within an autistic autism research group asking for collaborators to respond to the publication, specifically dealing with a number of flawed assertions contained the text.
These included:
-
- An attempt to formalise the concept of neurodivergence within a typology in which those who are neurodivergent fall outside of societal norms and those who did not are neurotypical, when societal norms are fluid and ambiguous at the best of times.
- The reduction of all other types of neurodivergence (such as different learning abilities and styles, tourettes or other atypical mental and neurological experiences) beyond those of autism or ADHD within the category of “other”, essentially disregarding the original principle of neurodiversity as encompassing the entirety of human experience; a very standard reductionist psychiatric/diagnostic approach to this vast diversity.
- Crediting of the term ‘neurodiversity’ to Judy Singer (an academic who was the first to use this in scholarship), when it had in fact been used online by autistic activists up to five years previously in the early nineteen-nineties.
The collaborative writing process within a neurodivergent research group can be complex, with much consideration given to the different sensory or communication needs of each individual as well as the ongoing stress they may be experiencing at any time. Often there are occurrences that would be considered rude or inappropriate, such as abruptly leaving a meeting with no explanation, were they to occur in an equivalent neurotypical workspace. Our team of writers and advisors included those who had a range of neurodivergent differences; autism, ADHD, dyslexia and mental health challenges, so as much time went into managing these with compassion and understanding toward one another as the actual writing itself. Although conflicting needs can cause frustration and difficulty, the shared experience of stigma and ignorance from others that neurodivergent people hold together is a strong foundation to work from to overcome them.
Additionally, the neurodivergent status of several contributors is not known publically outside of our research community (individuals holding prominent or senior academic positions would still experience discrimination were they to publically disclose). Others who worked on the response are publically known as autistic clinicians who have to be seen to not be challenging their professional status quo too much. This risk is such, that meeting recordings that included such individuals were transcribed and then deleted to avoid exposure of them to harm, professionally or personally.
We worked virtually using email, and shared documents for writing, commenting and editing, together with the occasional face-to-face video call. These styles of working have of course become much more prevalent since the Covid pandemic, however, their benefits to neurodiverse writing groups extend beyond the convenience of meeting without travel.
Neurodivergent communication preferences span many media and dimensions beyond that of written language. One of our group creates TikTok content incorporating signing for the deaf ADHD/autistic community, opening up lived experiences such as these to others who might be excluded because of intersectional disabilities. There was much lively debate about the inclusion of graphically based examples of neurodiversity and how far we would be able to challenge the publication boundaries of a very traditional medical journal such as the British Journal of Psychiatry and still be considered credible. On this occasion, an alternative format such as this was deemed to be too far to be included. Our work shows how different social and communication styles implicit in neurodiverse/neurodivergent groups demonstrate the value they can add to the democratisation of academic knowledge through variable dissemination, both from within the academy to the outside and from the outside in, via the insider/outsider perspective we hold and express through our output, whatever form it takes.
Overall, the process of containing the very different perspectives and styles within even a small neurodivergent group such as ours can be a challenge in and of itself, ensuring that they are all included in enough substance whilst still creating a coherent narrative. Nick and I worked on this refinement and translation process, with the agreement and ‘member checking’ of the wider team. This is how I came to receive the second author attribution in the writing process.
The first challenge we faced was the rejection of the paper’s original format as that of analysis, instead being considered as a commentary, with a word count and citation limit of half of what we had submitted. We decided as a group to reformat the original writing, to ensure a timely response to the original article with a commitment to submitting an expanded version at a later date. Upon resubmission, we received thoughtful reviewer feedback which improved the overall quality and style of the paper. These included challenges to “better capture the nuance and undoubted controversy in the field of biomedical vs social paradigms of neurodiversity and disability” which we managed successfully, whilst remaining within the wordcount and inclusive of the many different frames of neurodivergent reference included in our authorial group.
The final submission was well received by the BJP, whose editors and reviewers thanked us for our thoughtful and considerate responses both to their comments and the original paper. Although we were disappointed to have to shorten our original writing there was a commitment between a smaller group of those who contributed to further our thinking in a later piece, alongside others who produce and curate digital content for social media to adapt what we had created to make it suitable for audiences in these different contexts. We felt that this would be the best approach overall. In coming together we were able to express and explore a range of different ways of thinking, expressing and depicting our ideas. All are valid and worthy of use, however, the delineated nature of certain specialities like academic publishing means that, unfortunately, certain ways of being and communicating are still valued above others. We hope our work, as neurodivergent academics, will champion a breaking down of these barriers of in/validation between different styles and types of communication, along with greater acceptance of neurodivergent ways of being and knowing.