Post by Melanie Wilson (2018 Cohort)

This summer school was presented by Canterbury University in collaboration with the Leicester Castle Business School of De Montfort University, Leicester.
I attended on the Monday & Tuesday of this three-day event, as I had a family commitment on the Wednesday.
The presentations on the Monday were specifically addressing ideas around cyber-crime, social engineering and fraud. These are particularly relevant to me as my PhD is around increasing children’s abilities to identify and resist activities and approaches whilst online. I am addressing these from the perspective of enabling children to recognise attempts from others to engage in social engineering and to have the confidence and personal autonomy to reject anything they feel uncomfortable with, and to seek help where it is needed.
I am working with the Northamptonshire Police cyber-crime team on this and as such have a valuable insight into the challenges they have seen children facing as well as my own perspective as a psychotherapist working with children.
The summer school was the first of its kind to be run at Canterbury University and was led with great enthusiasm and skill by Jason Nurse. The summer school involved people from academia, social enterprise and industry which allowed a large variety of input and ideas to be expressed. Jason was skilful in accommodating discussions within the topics and I found that this approach, rather than the “talked at” approach, was very beneficial. Cyber-crime is a fast-growing field and the traditional approaches of academic study, which often take years to complete, are at risk of being overtaken as both technology and its associated exploitation by criminals proceeds at a rate far outstripping the slower traditional progress of academic work.
I feel this pace change was reflected well in the way the summer school was run. Some of the input could have been improved with more industry input to increase the pace and knowledge of the current challenges further, but I believe that Jason is aware of this and plans to address this in future events.
The first session explored the basics of cyber-crime reflecting on what forms it can take and highlighting how insidious it can be. It addressed the aspects of this area of criminology that are rapidly expanding and exploiting the tools that are available to enhance crime via technological means. One big take-home from this introduction and discussion was how fast this is developing in criminal circles where there are few restrictions and great financial gains to be made. This is at odds with the crime fighters and honest technological industry where there are checks and balances to be met in all circumstances which often results in a slower response which the criminal can exploit.
The Cyber Protect and Prevent Officer for Kent then gave us her perspective on how cyber-crime was affecting policing and the tensions between businesses which often wanted just to solve the issue and move on with business as usual and the desire to pursue cyber-crime as a crime with ramifications for the criminals.
The final session of the day looked at profiling cyber criminals and looking at how these criminals might be led into a perpetrator role. This is particularly relevant to my work because vulnerability leads to both perpetrator and victim activities and the two routes often share common factors.
At the end of the sessions we arranged to meet after dinner in a pub in Canterbury. Doing so was valuable as it provided a relaxed atmosphere in which to talk further with other attendees both about their work and that of others and gave a great deal of insight into the varying field that are involved with this ever-expanding and important field.
Tuesday morning looked at how cyber-crime is often underlined by psychological methodologies that criminals have learnt to use in order to perpetrate their crimes. We explored how social engineering uses a number of methods to elicit cooperation from people, utilising their vulnerabilities and often just their normal desires to help others and be nice. Again, this is an area that I focus on a great deal and feel addressing our ability to say “no” is fundamentally decreasing individuals’ vulnerability to such tactics. There is a noticeable difference in the psychological mechanisms that criminals exploit ruthlessly and the non-criminals’ tendency to trust.
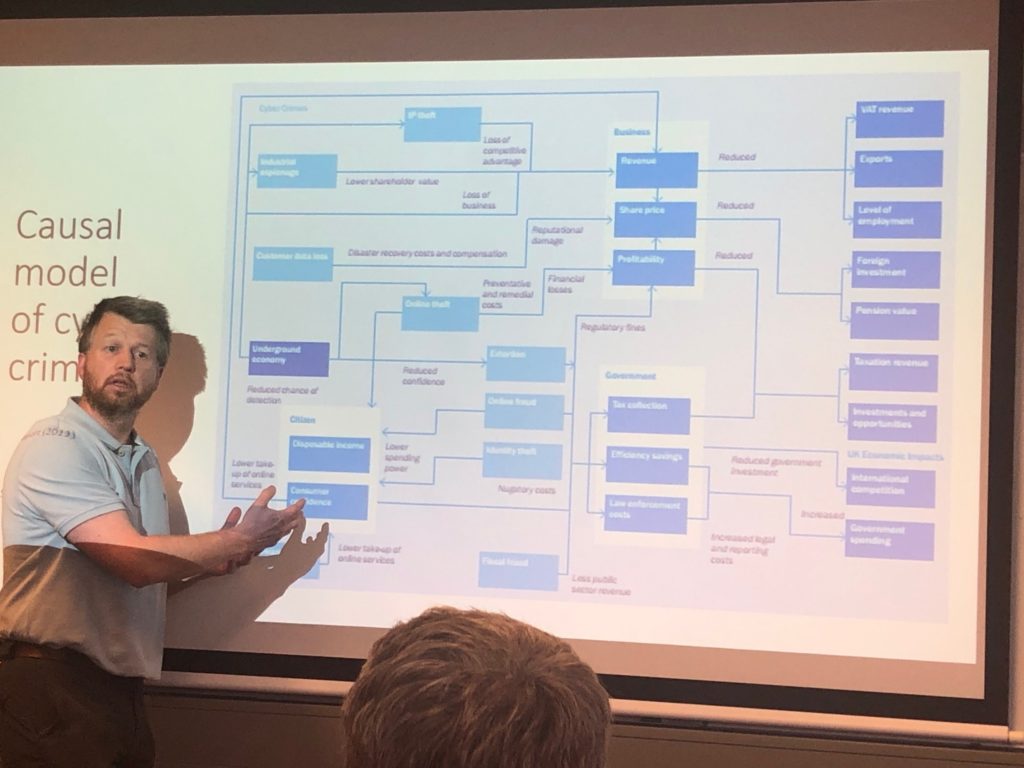
The afternoon sessions addressed the cost to businesses from cyber-crime. It was led by Edward Cartwright from De Montfort University and Anna Cartwright from Coventry University. It addressed business vulnerabilities and the attacks that businesses face daily, and the routes into the enterprise which are often indirect. The conflicts of security and running businesses were highlighted and discussed. The reality of end users often not rejecting companies following a breach and whether reputational damage is as damaging as is often thought. In Anna’s session we looked at the financial motivation for attacks and at what level the attacks and demands became profitable for criminals.
Finally, we looked at the problems and advantages in cyber security that Small and Medium Sized Enterprises face, addressing the challenges of this sector where often there are just a few individuals trying to complete multiple roles.
This summer school was fun. Where a learning experience is fun, lively and open to discussion, I feel far more is gained than from a situation where there is just one voice with very little interaction.
It greatly benefited from a range of perspectives and allowing those to be expressed and discussed. I feel everyone learned something from the variety and range of participants at the event and very much look forward to taking part next year.